-
Using Two Factor Authentication For Greater Protection
Your online accounts will be less vulnerable to hackers if your passwords are more secure.
It’s not difficult for crooks to get around passwords. They could gain access to your personal information, email, financial accounts, and credit card information, among other things, if they do this.
Thanks in part to the prevalence of cellphones, two-factor authentication (2FA) and two-step verification (2SV) make your accounts substantially more secure, often without much extra work.

What Is the Purpose of Two-factor Authentication?
Because passwords aren’t always as secure as you believe they are.
Phishing, brute force assaults, data leaks, and social hacking are just a few frequent workarounds for a single layer of authentication that is prone to phishing. * (For further detail, go to Types of Password Attacks.)
Worse, if you use the same password for multiple services, you’ll be able to access them all if you crack one.Because your password alone is no longer adequate to log in to your account, two-factor authentication adds an extra degree of security.
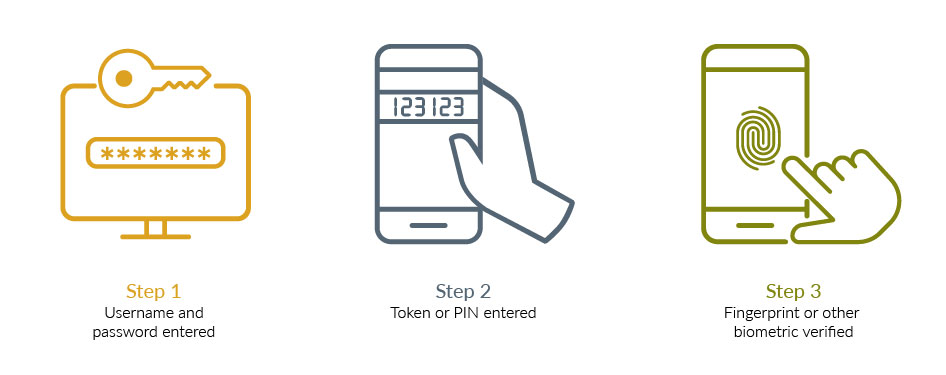
Two-step Security Is a Common Option.
Two-step verification and two-factor authentication have been revolutionized by smartphones. They work with the majority of the most popular options and are really beneficial because most of us are always on the go.
Some methods of authentication and verification are significantly more efficient or convenient than others, and some are far more secure than others.
Do a web search for the name of the website or service you wish to protect, as well as the words “two-factor authentication,” “two-step verification,” or their acronyms, to see what options you have.
Apps for Authentication
One of the finest trade-offs between security and convenience of use is free programs like Google Authenticator or LastPass Authenticator.
The software creates a new number code every thirty seconds or so once it is tied to an account. Open your authenticator app and enter the current number for the appropriate service when prompted.
By allowing you to tap a “authenticate” button, you may send your number code directly to the service.
It only takes a few seconds to break, and it’s exceedingly difficult for hackers to get into.
You may end up with many authenticator apps on your phone since certain websites or services require you to use their own app. To make it easier to find them, put them all in the same folder.
Question of the Day
Usually, secret questions are used to retrieve passwords that have been forgotten, and they aren’t very safe. You’re open to social hacking from anyone who clicks “forgot my password” if you choose a personal question, such as your mother’s maiden name.
PIN
Some PINs, like passwords, are more widely used than others, making you vulnerable to brute force attacks. Social hacking is another problem if your PIN is a significant date or number to you, or a niche-famous number from TV/movies like 1701 (a Star Trek reference).
Verification Through Text/SMS
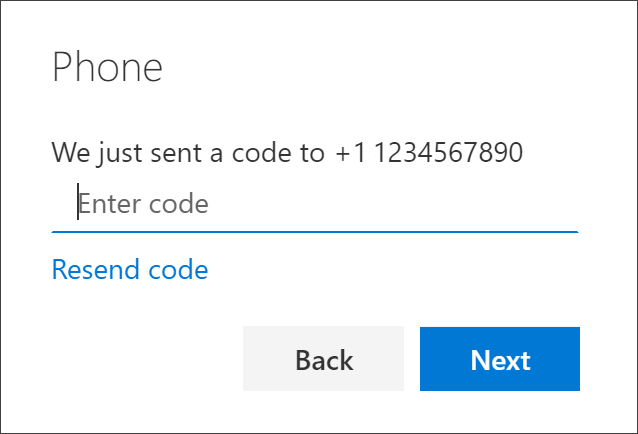 You’ll receive a one-time code by SMS when you create an account.
You’ll receive a one-time code by SMS when you create an account.One of the most ineffective ways to protect yourself is to use SMS messaging. In order to obtain the security SMS codes, fraudsters can trick your provider into moving your number to a new SIM card or provider so that they can receive them instead of you.
Another worry is that if your SMS notifications appear on your phone’s lock screen, someone who has your phone in their possession may be able to view the code without having to unlock it.
Verification of the Service of Instant Messaging (IM)
Because your IM account is more difficult to steal than your phone number, this is more secure than an SMS. Before you’re compromised, a fraudster needs to hijack your IM account first. You should be safe if that IM account is locked with an effective second step.
Because IM notifications appear on your lock screen, someone with your phone could view any code sent to you, just like SMS.
We have so many different ways we can always protect our data online. One is by setting strong passwords on our devices, emails. Enabling of two step verification like OTPs. #DataPrivacyWeekUG pic.twitter.com/yELRZyYhfw
— Mwiza Sophy 🇺🇬🇷🇼 (@MwizaSophy) January 28, 2022Verification Through Email
You’ll receive an email with a one-time code. This is only possible if your email account has previously been hijacked by a criminal. This might be a secure and simple way if your email account is locked down with second-step security.
The code may be displayed without unlocking your phone if your email alerts appear on the lock screen.
Authentication With a USB Security Key
 Governments and corporations used to use dedicated USB security keys, but now companies like Yubico are making them available to the general people. Plug the key into a USB port when prompted, and you’ll be able to complete the sign-in process.
Governments and corporations used to use dedicated USB security keys, but now companies like Yubico are making them available to the general people. Plug the key into a USB port when prompted, and you’ll be able to complete the sign-in process.Because they can’t be remotely hacked, their unique code changes each time they’re used, and newer models contain a sensor that detects if someone is touching them, security keys are incredibly secure.
You may be able to bypass the password entirely and solely utilize the key as a means of authentication, but this is still uncommon.
A USB stick and some specific software can also be used to produce your own security key. It’s difficult to do, and the best programs for it are expensive.
USB keys, on the other hand, are simple to lose and inconvenient if your USB ports are occupied or awkwardly positioned, and restricting if your security key doesn’t work with your phone, and if your security key doesn’t work with your phone.
To make things easy for yourself, it’s also tempting to leave them plugged into a laptop, tablet, or phone. However, if you lose that gadget, the key will be given to whoever finds it.
What if I Forget to Bring My Authentication Card?
There are usually ways to recover your log-in information if you lose access, whether you’re using an authentication app, fingerprint ID, or some other 2FA or 2SV approach.
When you first sign up for an authentication app, you’ll often be given a code or a collection of codes to write down. If you wish to be able to recover any lost sign-in information, keep these handy.
A PIN or a secret question-style “I forgot my password” system, for example, could be a less secure alternative to a fingerprint ID.
If you lose access to your authentication or verification credentials, any system you sign up for should include instructions on how to retrieve your accounts. Check on them before jumping in if you’re concerned about losing access.
Methods for Stealing Passwords
Phishing
You are tricked into handing over your personal information, login names, and passwords by phishing. This can be done in a variety of ways, and even hardened security experts can be fooled.
Attacks with brute force
Brute force attacks, which are one of the most fundamental types of account hacking, make millions of educated guesses as soon as possible. Before going on to dictionary words and common phrases, they tend to try common passwords first, such as “123456,” “password1,” and “iloveyou,” among many others.
A strong, one-of-a-kind password can protect you from a brute-force assault, but it’s no substitute for 2FA or 2SV.
Breach of data
Your account with a service, organization, or website could be a target for hackers. They can take your username and password from a database and use it to log in from afar. Data breaches may affect anybody, from small websites to giants like Facebook.
Hacking Information through social
In what ways are your social media accounts open? Hacking your social media accounts involves someone looking up public information, such as what you or others on social media list, and using it to break into your accounts.
If your password contains something personal, such as a family member’s or pet’s name, it can be deduced with a little digging.
For more tech news, articles, reviews, tips and more check out Jafworks.com