-
Fosters and Partners Adopts Spot the Boston Dynamics Robot Dog
As we enter the era of Artificial Intelligence and the “Internet of Things” (IoT), the world is fast moving onto new technologies that would bring unimaginable transformation in many industries. In one such recent development, Spot, the Boston Dynamics’ robot dog, was adopted by the world’s leading architecture firm, Foster and Partners, as a construction site inspector. Spot Robot Dog is currently assigned to the Foster and Partners’ Battersea Roof Gardens Project. The development is an extension of the wider development in the area surrounding Battersea Power Station, a defunct power plant undergoing repurpose renovations.

Spot, the Boston Dynamics Robot, is used by the architecture firm in London’s Battersea Roof Gardens Project to test its capability and potential for future projects. So far, the results have been more than positively surprising. Spot Boston Dynamics Robot can be remotely controlled and can be programmed to follow a predefined route on the site. It has been designed and developed by Boston Dynamics in collaboration with the Foster + Partners’ Applied Research and Development Group. The firm specifically designed maps and missions for Spot Boston Dynamics robot dog to gather and collate data from the assigned site.
Spot, the Boston Dynamic Robot Dog, rerun its route on site at weekly intervals. The architecture practice said the data sent back by Spot has been exceptionally helpful in creating a sequence of comparable and consistent data. It is especially due to the robot dog’s ability to trail in rough and hazardous terrain that humans can’t scan accurately. One of the technologies used by Spot Robot Dog is the 3D scanning technology to monitor construction progress by doing precision scans at regular intervals.
It then checks the scan results for any errors while matching it with the already programmed architectural plans. The experts at Foster + Partners said that with the help of data collected by Spot Robot Dog, the processing and scanning time at sites had reduced drastically. It helps with project completion as per the schedule and limits the use of resources, saving time and money considerably.

Spot has been earlier used at a Japanese Construction site, so it is not completely new in the construction business. With its four-legs, it can climb stairs, manoeuvre through rough and patchy terrains and work semi-autonomously or be controlled remotely. On its first day at the site, Spot the Boston Dynamics Robot Dog was warmly welcomed with its own ID card and a lanyard. The Foster and Partners also used Spot Robot Dog to create a “Digital Twin” of its London Campus to compare design and build reality, which would eventually help make architectural changes to the space to improve efficiency.
Martha Tsigkari, one of the Partners at Foster and Partners, said regular scans by Spot Robot Dog allowed the firm to check on the project’s progress. It helped keep up with the timeline and compare consistency against the BIM (Building Information Modelling) Model. With the efficacy of Spot the Boston Dynamics Robot being admired globally in the construction business, it won’t be wrong to say its role at the building sites will only increase with time.
For more tech articles, reviews, advice and news read Jafworks.com
The below video shows Spot being welcomed into the office and then presented with its own Foster + Partners lanyard and ID card, before accompanying architects around the site and performing a scan.
The information that Spot collects is then sent back to Foster + Partners and used to build and update a “digital twin” model of the project as it is built. The model can be used to compare the design to the built reality.
-
PlayStation 5: Sony Finally Reveals the Long-awaited Console
It is finally here with us. Well, not the actual product, but at least we now know what the Sony PlayStation 5 console looks like.

During the PlayStation 5 games reveal that aired on June 11, Sony also let out the design of their latest console that’s due later this year. Though that was not the initial plan, Sony had to culminate a surprise release of the Ps5 design, probably to prevent a possible design leak.
We know so far that the PlayStation 5 will be the most powerful console created by Sony, and here’s everything you need to know about this powerful machine.
PlayStation 5 Specs
According to Mark Cerny the lead system architect at Sony, the PS5 will feature some powerful specs; a 16GB GDDR6 RAM, a custom 825GB SSD with expandable storage, an inbuilt 4K Blu-ray drive, an AMD Zen 2-based CPU that has eight cores each running at 3.5GHz to facilitate lightning-fast processing.
Design
The PlayStation 5 has ditched the typical monochrome color scheme used in its predecessors and comes in a white and black design that’s also shared with its DualSense wireless controller.
It is important to note that the console will come in two editions, a normal version and a digital version. As expected, the normal version will use disc drives to run games while the latter will only play digital games. According to a random poll on twitter, it seems that most people would still prefer the Disc drive ps5 over the digital edition.
The creation of a digital version is an indicator that console manufacturers are shifting their focus to a future without physical media.
Price
Sony is yet to confirm the price of the PS5, and that’s because they are yet to discuss the actual cost, according to Hiroki Totoki, Sony’s CFO.
“What is not very clear or visible is because we are competing in the space, so it’s very difficult to discuss anything about the price at this point of time and depending upon the price level, we may have to determine the promotion that we are going to deploy and how much costs we are prepared to pay,” Totoki explained
However, Jim Ryan has already hinted that the Sony PS5 price will most likely be a bit expensive compared to its greatest rival currently, the Xbox Series X. Also, the fact that the PS5 will feature some high-end components will most likely attract a high price tag.
When is the PS5 release date?
According to Sony, the console will be released during this year’s holiday – that’s somewhere between October and December 2020.
What Games Can I Play on It?
Even though the console is incredibly powerful and aesthetically appealing, the games to be played on it bring out all the difference. The event that aired on June 11 was supposed to be a game launch and not the console reveal, and some of the games to be played on the PS5 include, the new Marvel’s Spider-Man: Miles Morales, Gran Turismo, Returnal, Sackboy A Big Adventure among others.
I Already Own a Playstation 4; Can I Use My Games on the Playstation 5?
Another beauty about the Ps5 is that it will be backward compatible, meaning you can play your Ps4 games on it. However, Sony only stated that the PlayStation 5 would support “almost all” PS4 games, and did not confirm the earlier generation games.
-
Spot the Robot Dog Roaming ‘Robodog’

It is no secret that the Coronavirus (COVID-19) has greatly affected people’s lives all around the world. Schools being shut down and companies advising their employees to work from home are some of the effects of this global pandemic.
One of the notable things happening at this trying time is the continuous emphasis on “social distancing.” Social distancing is a term used to describe a way of people maintaining a safe distance, usually one metre, between each other. It is highly emphasized as it is critical in reducing and possibly stopping the spread of Coronavirus. It is because of this that Boston Dynamics, a robotics design firm, built a remote-controlled four-legged Robodog known as Spot.
Spot (the Robodog) has been enlisted by the Singaporean authorities to help in curbing the spread of Coronavirus by advising cyclists and joggers to stay apart. The dog conveys the message in a soft feminine voice using the English language. As it goes around you will hear it say things like “For your own safety and those around you, please stand at least one metre apart. Thank you.”
The yellow and black machine is not only programmed to convey messages. Boston Dynamics equipped the Robodog with top-notch cameras and analytics tools that help in estimating the number of people in the park.
However, the presence of a robotic headless dog roaming around has not been without controversy. According to a video posted by “The Straits Times,” the dog is seen to cause a lot of confusion and fear among several park-goers even those who are several metres apart. Basically, park-goers are noted to be recoiling every time the dog passes close to them.
Some people are said to be against the use of the dog due to its capability to take photos and record videos. However, the authorities have addressed people’s concerns stating that the dog does not track or recognize specific individuals. The authorities insist that the dog’s sole purpose is to record the general number of individuals in the park, and that is all it does.
Even with all of this controversy, the dog’s role in sensitizing the public and recording data is mainly geared towards turning the nation’s COVID-19 situation around. With a population of about 5.7 million people, Singapore has recorded 21,000 cases of Coronavirus. This is among one of the highest reported cases in Asia.
According to relevant sources, the numbers in Singapore have spiked due to mass infections among migrant workers who are living in cramped dormitories.
Robodog in Hospitals
Apart from parks, the Robodog has also been deployed in hospitals, particularly the Brigham and Women’s Hospital in Massachusetts. The aim of this is to help the medical practitioners that are on the frontline in the fight against the Coronavirus. With a two-way radio and an iPad strapped to it, the headless Robodog serves as a telemedicine platform provider. Some of the areas it is heavily used are; triage tents and parking lots.
For more tech articles, reviews, advice and news read Jafworks.com
-
Do You Suspect One Of Your Neighbours Is Leeching Off Your Wi-Fi?
Here’s what you can do to ensure that this doesn’t happen in future!
Are you not able to explain why your wireless internet connection has been feeling slower than usual? It may be that your Wi-Fi is being stolen by someone around you.If anyone is using your WiFi without your permission they are stealing from you. Despite what the below Tweet says.
— Quarantined Mystic (@ShinyHuntMystic) September 29, 2019
If you think this is happening you can do the following:
1) Log into your router control panel, if you don’t know the credentials, it’s typically admin/admin. Otherwise, check your router for any written labels that looks like a username and password combination.
2) Change your WiFi password to something of 16 characters, with no words. Make sure it has numbers and symbols, and that you can remember the password.
3) Make sure you use WPA2 and TKIP or AES.
4) Disable WPS (Pin). You should never have this feature enabled.
5) Don’t share your new password with anyone.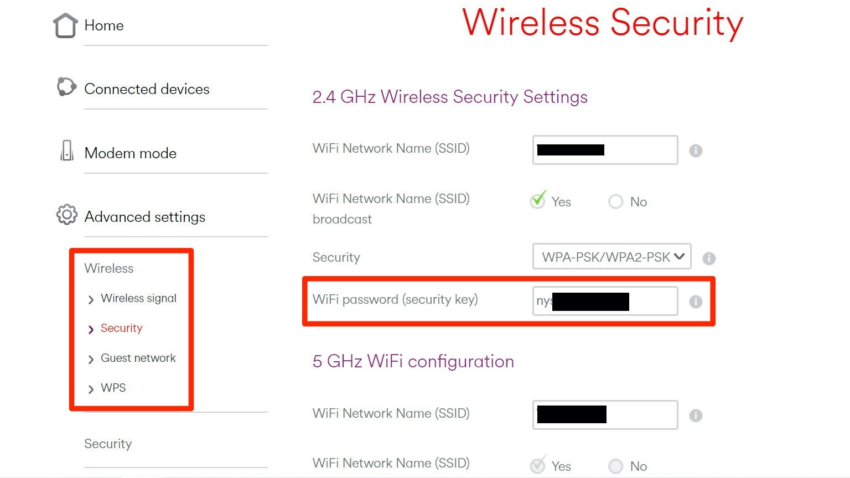
Within your router’s control panel, there will also be a page that shows you the list of connected devices. This will be different on every router but it is usually found under “DHCP” or “NAT” categories and this is the ideal way to check for connected devices.
However, some routers don’t have this feature, and if this is the case with your router you may want to use a scanning tool instead.
A scanning tool is software that runs on your computer and it scans the Wi-Fi network that you are connected to for active devices and displays these connected devices as a list.
Unlike router web interface tools however, scanning tools have no way of listing devices that have been connected, but which are not currently connected or are offline. You will only see connected online devices.
Important Note:
When you change the password on your router, none of your devices will connect or work with your WiFi until you change the WiFi password on them as well.Changing your Wi-FI password often is a good idea, especially if you have given out your Wi-FI password to other people such as to neighbours or friends who are visiting you. By changing your password regularly you can be sure nobody will be able to continue using your WiFi for years.
For more tech articles, reviews, advice and news read Jafworks.com
-
How to Keep Your Smartphone Clean During the Coronavirus Outbreak?
With the recent outbreak of the Coronavirus, you never be too safe from it. The virus which spreads easily from one person to another is mostly grounded and not like any other airborne virus that takes a lot of time in air. One place the virus is highly likely to be on is on your smartphone.
Using Wipes

Wipes dipped in isopropyl alcohol which has a significant concentration of the alcohol is one way of getting rid of the virus which might have made its way to your smartphone’s surface. You just have to ensure that moisture does not get to the delicate components of the phone. You should avoid using pure alcohol or methylated spirit as it has some negative consequences.
Stuck Dirt
This is the use of sticky tape to remove dirt that is located on those difficult to reach spots. These spots include the areas around the speaker or along the sides of the charging port. This can’t be clean with a wipe and might be housing the deadly virus.
Using A Microfiber Cloth

A quality type of microfiber cloth can get the trick done in case you do not want to use alcohol or any complicated stuff. You can purchase an excellent quality of this from online retailers. The microfiber cloth is a simple way of cleaning your phone and is also highly effective as it gets the job done with the least effort applied.
UV Phone Sanitizers
Phones have been proven to carry the most load of bacteria, more than even in the case of toilet seats. The bad news is that toilet seats get washed and cleaned more frequently than the phones. Some people have never even taken time to clean their phones which they have had for more than three years or so. Therefore, using a phone places one at high risk of coming into contact with the coronavirus. UV phone sanitizers would help get rid of bacteria and even the virus which might be on the surface of the phone. For instance, phone soap is designed to make use of UV-C light to break down the virus.
Using Cotton Swab

This would be ideal if you want to thoroughly clean the hidden part of your phone that are hard to reach. Spots such as the headphone jack, the memory card and sim card slots gather a lot of dirt which include some harmful bacteria. Getting a good cotton swab will be highly effective in cleaning this parts.
While undertaking the cleaning of your smartphone using any of the above methods, it is recommended that you have a safe mask over your nose and mouth. You should also sanitise your hands after completing the cleaning process of the smartphone.
The coronavirus has the ability of staying on a surface for more than forty-eight hours. Therefore, unless you clean your smartphone well, it might be an agent of the transmission of the virus. The above methods are effective ways of keeping one’s smartphone clean and free from the coronavirus.
For more tech articles, reviews, advice and news read Jafworks.com
-
P2 Facemask; Tips on How to Buy the Best Facemask for Smoke Protection

As the strong winds continue to spread across Australia, so does the wildfire. If you thought that wildlife was the only thing affected, then you must be tripping. A small digging over your science notes should remind you that the smoke from bushfires isn’t good for your health as well. In response to the severe haze, many people have turned to filtered face masks to help cover the pollution.
What many people don’t understand is that not all masks are effective when it comes to protection against the harmful smoke. The good news is that with a P2 facemask, you can be sure of full protection against the harmful components found in the smoke from bushfire.
What Is a P2 Facemask?

If you have been to a construction site, then you already know what a P2 facemask is. Yes, they are those face masks that builders wear during work. P2 facemasks, also known as a PR respirator is a mask designed to filter particles from the air while reducing the spread of airborne diseases. The builders depend on these masks to cover themselves from the harmful chemicals that may be coming from the bushfire.
Based on research, the smoke from wildfires is known to contain P.M 2.5 particles. These particles are known to be harmful to one’s health if inhaled. It’s for this reason that you are always advised to have a P2 mask with you always to cover yourself against the harmful particles.
How to Buy the Right P2 Facemask
-
Know Where to Buy
Accessing P2 facemasks shouldn’t be a problem as the masks are readily available. If you are looking for one, you can start by checking a hardware store near your location. You can ask the staff over there to help you with locating the right mask. Also, you can buy the gear online via stores such as Amazon.
-
Consider the Prices
With the harsh economy, every penny is worth counting. When buying a P2 facemask for cover against smoke, it would be best if you considered the prices. The prices at your local hardware can never be the same as those in the stores such as Amazon. Over Amazon, you are likely to find competitive prices as opposed to the physical local hardware.
-
Consider the Designs

Covering yourself against smoke doesn’t have to be boring. You don’t have to look like the others while walking around the streets. Therefore, you can shop around for fancy P2 facemasks. Most local hardware does have these masks in various designs. Also, online stores such as Amazon have face masks from various manufacturers. Therefore, you can shop for that one design that matches your taste and preference.
-
Consider the Size
One thing you should note when shopping for a P2 facemask is that the mask comes in three sizes. That is, there is small size, medium, and large size. Therefore, when shopping, you must consider the right size for your face. To ensure that you get the correct item, it would be best if you tried fitting the mask before leaving the hardware, for instance.
Note: Although a P2 face mask is said to be safe cover against smoke. It can only be effective if it fits you right and there is an air-tight seal around the mouth and nose.
-
Consider Time
How urgently do you need the facemask? This is one significant question you ought to ask yourself before you start shopping for your gear. One thing to note is that shopping on Amazon can take longer as opposed to walking into a physical store. Therefore, although online stores such as Amazon tend to amazing deals, at times they might not be efficient. If you are in much need of the face mask, then you should consider walking into a store and getting the mask by yourself from the store.
Conclusion
With the frequent bushfires in Australia, you ought to protect yourself against the smoke. P2 face masks are known to help with covering oneself against the harmful components contained in this kind of smoke. By reading this article, you will learn everything about the P2 facemasks from the definition to the usage. Read through the entire piece to gain tips on how to acquire the gear with fewer hustles.
References
- https://www.lifehacker.com.au/2019/12/masks-smoke-bushfires-nsw-where-to-buy/
- https://www.healthdirect.gov.au/blog/do-face-masks-protect-you-from-bushfire-smoke
- https://www.gizmodo.com.au/2019/12/where-to-buy-the-right-face-masks-for-smoke/
- https://www.finder.com.au/wearing-a-p2-face-mask-for-smoke-protection
-
-
It Was a Matter of Time: Blockchain Technology Is Being Hacked

What Is Blockchain or Blockchain Technology?
The famous blockchain sounds like a medieval construction. But in reality it is a new type of digital accounting book and distributed to the forefront of computer science.
Blockchain vs Bitcoin
Perhaps you have heard the media describe blockchain technology as “the technology that drives Bitcoin.” Or you may have heard that large banks and companies are interested in using blockchain technology, but not Bitcoin itself… So, if the blockchain or blockchain is not Bitcoin.
What Is Blockchain Exactly?
Let’s go for start at the beginning, with the invention of the blockchain. Which is directly linked to what is Bitcoin. “Satoshi Nakomoto” is the pseudonym of the mysterious creator of this technology, whose true identity remains unknown to this day.
In 2009, Satoshi launched blockchain technology to the public under free Bitcoin software. In addition to a technical whitepaper that described the system.
The revolutionary Satoshi system allows an open computer network to create and share valuable data in an incorruptible manner … without the need of any central authority to keep the data synchronized and accurate.
For this reason, the blockchain is sometimes called “decentralized or distributed book.” It works strictly peer to peer (or peer to peer without intermediaries). Similar to file sharing systems on the internet like BitTorrent.

Bitcoin Blockchain
So, if Bitcoin operates through a public accounting book …
The bitcoin blockchain, or bitcoin blockchain, is the mechanism that keeps all participants in consensus. And avoid accounting errors, whether accidental or intentional.
Bitcoin Blockchain Components
Satoshi merged several existing technologies to create blockchain technology:
1.The decentralized network architecture is the first component.
2.The second element is asymmetric cryptography (or public key cryptography). No need for participants to share their private codes (private keys).
3.The third and final element is the proof of work hash. Which serves as proof that the required computational work was performed.
Actually Satoshi did not invent any of these technologies, but by combining them, he created the unique formula called blockchain or btc blockchain.
Blockchain Technology
Fortunately, you do not need to be an expert in each of these contributing technologies to have an overview of blockchain. You just have to know that they are important gears in the digital machinery of the blockchain.
First Blockchain Application
The first application of blockchain technology was of course monetary. The creation of a fully secure online accounting book that tracks the ownership of the “digital gold” known as Bitcoin.
In the future, blockchain technology is likely to be the way society tracks properties of all kinds, such as:
- Actions
- bonuses
- propeti writhing’s
- even legal contracts …
Since this technology has enormous disruptive potential in a large number of industries. In fact, there are many initiatives exploring different blockchain applications in different industries.
But for now let’s focus only on Bitcoin and its monetary application …
How is the Bitcoin blockchain in a public anti-fraud registry that faithfully records transactions without any central control entity that keeps its participants honest?
How Does Blockchain Work?
You may have heard about Bitcoin miners, if not… Check out our video, “ What is mining Bitcoins? ”Which easily explains how mining works on the Bitcoin network.
But in summary, basically the miners record all Bitcoin transactions in data packets known as “blocks.”
These blocks are linked in a linear sequence using a special code. Each transaction in a block enters into the formation of this code … And the final result is recorded in that block.
Then the next block forms a new code and includes the code from the previous block and so on. The chaining of all the blocks together guarantees the permanence of the previous transactions … You cannot change the information of the previous blocks without also changing all the subsequent blocks.
Together, these linked blocks form a growing public record with all Bitcoin transactions since its inception … Known of course as the blockchain or blockchain.
Blockchain Example
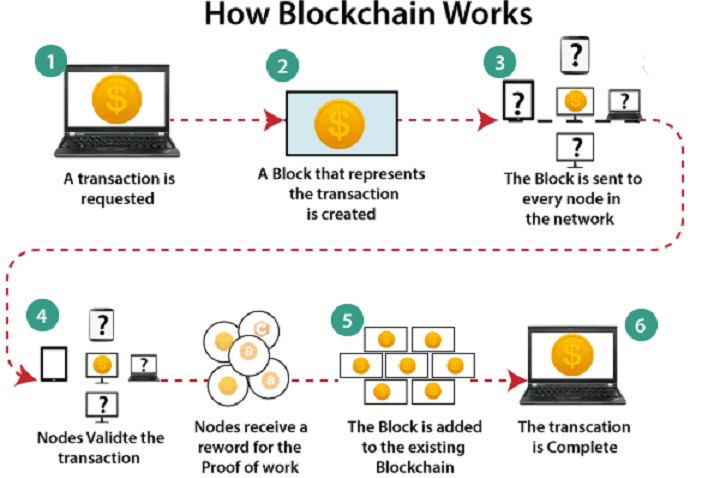
Now that the term makes a little more sense, I will explain the blockchain in greater depth. Imagine this example:
Let’s say you send some bitcoins to a friend using a Bitcoin wallet , your transaction will be retransmitted across the entire Bitcoin network.
Everyone will see that address A (your address) is trying to send that amount of coins to address B , (your friend’s address).
People who operate the so-called “complete nodes,” that is, Bitcoin software clients that store the entire blockchain … will quickly receive information about your transaction.
Full nodes verify your transaction information against their own stored copy of the blockchain. Therefore, the full nodes check whether the address A has enough Bitcoins to pay the specified amount to the direction B .
They will also check other new transactions. To verify that A is not trying to send the same currencies simultaneously to address B and also C or to addresses C, D, E and so on.
This particular form of fraud is known as a “double expense.”
It is important to note that double spending was a major technical problem in computing … Since it prevented the reliability of peer to peer electronic money (or peer to peer without intermediaries). Until Satoshi’s blockchain solution appeared.
Who Writes Blocks In Blockchain?
Double spending aside, let’s return to our example:
If your transaction is approved by complete nodes, it will soon be transmitted to a special type of complete node. Although sometimes your transaction will reach this special node first.
These special types of complete nodes have the ability to register transaction blocks in the blockchain … Guess what these special nodes are called? These are the famous “miners” of Bitcoin.
Blockchain like Bitcoin, in which miners compete to write the next block in exchange for a reward … It is the type known as “Proof of Work” blockchains.
The work in question refers to the hash or resolution of a mathematical equation. Which reduces information of any length to a fixed length.
Difficulty Settings In Bitcoin And Blockchain
The Bitcoin protocol adjusts the difficulty of this equation periodically and automatically. To satisfy the amount of computing power available in the network for its solution.
These difficulty settings ensure that a new block is written every ten minutes on average. No matter if more miners enter or leave the Bitcoin network.
At the beginning of Bitcoin the difficulty was low. And the blocks could be solved reliably using only a laptop. As the value of Bitcoin increased, so did the difficulty of mining. Since this became increasingly competitive.
Today, mining is done with specialized hardware. Hosted and refrigerated in huge data centers or mining farms like this one:
It Is No Longer Infallible
In total, hackers have stolen almost $2 billion in cryptocurrencies since the beginning of 2017, mostly at exchange sites, and that is what has been publicly disclosed. These are not just solitary opportunistic attackers, much less: it is presumed that there is a whole structure behind.
We shouldn’t be surprised. Blockchains are particularly attractive to robbery because fraudulent transactions cannot be reversed as they can often be in the traditional financial system.
On top of that, we have known for a long time that just as blockchains have unique security features, they have unique vulnerabilities that they were a matter of time before they were left at the mercy of the friends of others.
How Do You Hack A Blockchain?
A blockchain is a cryptographic database maintained by a network of computers, each of which stores a copy of the most updated version. A blockchain protocol is a set of formulas that dictates how computers on the network, called nodes, should verify new transactions and add them to the database.
The protocol uses cryptography, game and economics theory to create incentives for nodes to work to secure the network instead of attacking it for personal gain. If configured correctly, this system can make it extremely difficult and expensive to add fake transactions, but relatively easy to verify valid ones.
But the more complex a blockchain system is, the more ways there are to make mistakes when configuring it. Earlier this month, the company in charge of Zcash – a cryptocurrency that uses extremely complicated mathematics to allow to clients make transactions in private – revealed that it had secretly fixed a “subtle cryptographic defect” that had been accidentally incorporated into the protocol. An attacker could have exploited it to make an unlimited counterfeit Zcash. Fortunately, nobody seems to have done that.
So, in theory, the way to attack a blockchain protocol depends on having made mistakes to program it, but it also has to be a very lucrative robbery because renting enough data-mining equipment to attack, for example, bitcoin, costs around $ 260,000 per hour. If it is not successful, it is lost money.
By mid-2018, the attackers began launching 51% attacks against a series of relatively small and slightly traded currencies, such as Verge, Monacoin and Bitcoin Gold and stole an estimated total of US $ 20 million. Months ago, hackers stole around $ 100,000 using a series of attacks on a currency called Vertcoin. The blow against Ethereum Classic, which raised more than the US $ 1 million, was the first against one of the top 20 currencies.
References.
https://www.technologyreview.com/s/612974/once-hailed-as-unhackable-blockchains-are-now-getting-hacked/
https://yro.slashdot.org/story/19/02/22/2239210/once-hailed-as-unhackable-blockchains-are-now-getting-hacked
https://www.reddit.com/r/technology/comments/at1svv/once_hailed_as_unhackable_blockchains_are_now/ -
5 Best Android Smartphones of 2019
In 2019, we witnessed the largest number ever of interesting and high-performance smartphones with improved specifications and features. Brands from all over the world rolled out either a brand-new range or a new model within the existing range, with the improved overall design, specifications, and even user interface. So, writing this article on my favorite and probably best 2019 smartphone proved to be quite a challenge for me.
5. Google Pixel 4

Having personally used it for almost six months, I confess that I am a big fan of its design and in some use-cases of the camera too. Apart from the stock android experience that unfortunately is becoming increasingly rare lately, the access to unlimited storage for all my pictures and videos and this without any compression is simply amazing especially considering the fact that the camera is quite fun to use and in some cases, the image quality is incredibly superior to most smartphones I’ve ever had. Priced at AU$1049, Google Pixel 4 is a perfect smartphone for individuals who are looking for a mean to experience the stock android interface and get access to some Google-specific feature sets.
But, despite all its features, there’ s just too much missing. It doesn’t have an ultra-light camera, really poor battery performance, and a bizarre lack of internal storage.
4. Nokia 9 PureView

Nokia 9 is the most high-end smartphone released by Nokia in 2019 and is definitely a lot of fun to use. Priced at AU $1,099, it features a powerful Penta camera setup capable enough of capturing fantastic raw images with extreme detail, which you can tweak to your needs afterward. It also features a fantastic sleek, yet in some way, very minimalistic design that definitely feels premium in every way. Sadly, even though it features an impressive 120 GB internal storage, 6 GB RAM coupled with 3320 mA battery, Nokia 9 uses an outdated processor compared to similarly priced competitors. Moreover, the Penta camera setup doesn’t have any telephoto lens, which might prove to be a decision-making factor for many smartphone enthusiasts.
3. OnePlus 7T Pro

A very deserving of a spot on his list is the OnePlus 7T Pro. When this company started, they were in a league of their own in terms of offering the absolute best hardware at a much lower price. But recently, this whole category of cut-price flagships has become congested. OnePlus is no longer one of the cheapest phones to have the best hardware, but they’re becoming one of the better ones.
With OnePlus 7T Pro, you’ve got really lightfast, up to date software plus a lot of love has gone into this display. It’s dazzling! And as is becoming a bit of a trend this year, its display has a fluid 90 Hertz refresh rate. Besides, even though far from the cheapest now, the OnePlus 7T Pro is still cheaper than a lot of its counterparts. Priced at nearly AU$ 890, this smartphone lets you experience one of the best fluid touchscreens coupled with superior performance powered by Qualcomm Snapdragon 855 processor, 8 GB RAM, and 256 GB internal storage. Moreover, featuring wrap charge 30, it lets you charge your smartphone to nearly 90% in just over 20 minutes.
2. Vivo NEX 3 5G
Would you want to have a futuristic curved display smartphone? Well, then you definitely need to check out Vivo NEX 3 5G. If you fall in a category of smartphone enthusiasts who absolutely adore curved displays, then Vivo NEX 3 5G’s display curve is so dramatic you’ll find yourself letting out a little sigh of admiration every time you pull it out your pocket.
Moreover, to shoot in the deal further, it has got a great specification featuring a really great 64-megapixel camera, a powerful 4500 mA capacity battery and the price tag still $ 1000 less than the Apple’s finest model.
1. HUAWEI Mate 30 Pro

First on our list is surprisingly HUAWEI Mate 30 Pro, which, despite the ban from the US government, has emerged to be one of the most successful smartphones of 2019. What I personally like about this smartphone is its asymmetrical design on the front, along with its camera, which is absolutely fantastic even in a lowlight environment. In fact, from my personal experience, I believe its camera is as capable in the night as it’s in the day. Then it has got the newest 5G networking enabled Kirin 990 chipset, 4500 mA battery, 8 GB RAM, 256 GB internal storage. At a price of AU$ 1599, HUAWEI Mate 30 Pro brings you a unique smartphone experience, unlike anything you have ever experienced before.
-
Facebook App Uses iPhone’s Camera When You Are Scrolling Your Feed
Joshua Maddux has unearthed yet more controversy around Facebook. Joshua has discovered that the Facebook iOS app was keeping the camera app on his iPhone active even while he was scrolling through his feed. This was reported by ZD Net.
Other app users also confirmed these findings and Joshua also found the same bug on five other devices that he tested.
Found a @facebook #security & #privacy issue. When the app is open it actively uses the camera. I found a bug in the app that lets you see the camera open behind your feed. Note that I had the camera pointed at the carpet. pic.twitter.com/B8b9oE1nbl
— Joshua Maddux (@JoshuaMaddux) November 10, 2019
This glitch or bug has only been only appears to be found on iPhones that are running iOS 13.2.2. There have been no users have been able to replicate this on devices that are running the iOS 13.1.3.
What is not clear is how long this bug has been in existence for and it is not clear if this has been intentionally done. There are a few users that are currently running iOS 12 and they have also discovered that the camera app is active while they are using the Facebook app.
This glitch or bug doesn’t seem to happen when you have not given Facebook’s app permission to access or use your device’s camera. Additionally this bug doesn’t seem to be affecting the Android version of Facebook’s app.
While there are not many people who would accuse Facebook of being over the top in regards to protecting user’s privacy it is more than likely this is an unintentional happening. However it possible that there are many people who will question this.
Cnet reported that Guy Rosen, Facebook’s vice president of integrity, tweeted that this appears to be a bug and that Facebook was looking into the problem.
Found a @facebook #security & #privacy issue. When the app is open it actively uses the camera. I found a bug in the app that lets you see the camera open behind your feed. Note that I had the camera pointed at the carpet. pic.twitter.com/B8b9oE1nbl
— Joshua Maddux (@JoshuaMaddux) November 10, 2019
.
Rosen Tweeted later that Facebook is submitting a fix to the App Store.
Users notice Facebook’s iOS app accesses the camera as they do unrelated things like scrolling their feeds; one workaround is to revoke app’s camera permissions (@alfredwkng / CNET)https://t.co/iRsYbWR8uHhttps://t.co/HiFdj1XWEp
— Techmeme (@Techmeme) November 12, 2019
“We recently discovered our iOS app incorrectly launched in landscape,” Rosen said. “In fixing that last week in v246 we inadvertently introduced a bug where the app partially navigates to the camera screen when a photo is tapped. We have no evidence of photos/videos uploaded due to this.”
He also confirmed that Facebook did not upload or use any photos or videos while it was running in the background, stating that it was in preview mode.
Should you be a user of the official Facebook app on your iPhone we suggest update the app or you could also revoke the the Facebook app’s permissions to access you camera and perhaps all other permissions from this app.
-
The Netflix Scam Going Around Australia
Online security is again under the microscope as a new phishing scam impersonating Netflix has been appearing around Australia. In this scam the perpetrators attempt to obtain your sensitive customer data. Here’s what has been reported and what you should be aware of .
Lifehacker Australia have also noted that this scam looks legitimate with official looking Netflix branding and links that appear to lead to Netflix’s genuine website.
Variations of the scam uploaded by other users show some emails claiming the scammers could not authorise payment resulting in a suspended or expired membership.
Aussies have been warned by Scamwatch via Twitter, they have warned on the dangers of opening and interacting with this emails.
Scammers are targeting Netflix customers in an email scam claiming your payment info needs to be updated. Don’t click on the link. Go directly to the website to check your account details https://t.co/uTcmlvPrrV
— Scamwatch_gov_au (@Scamwatch_gov) November 4, 2019
This scam has also been reported by many Aussies on Twitter and also on Reddit. The emails do appear genuine as Netflix’s branding has been replicated well. The email requires receivers to update their payment information due to an issue with their account.

Scamwatch warned people to not click on any links that are provided in these scam emails. Instead if you want to query the email go to Netflix’s official site and check for any problems if you have concerns.
“Scammers are targeting Netflix customers in an email scam claiming your payment info needs to be updated,” Scamwatch Tweeted. “Don’t click on the link. Go directly to the website to check your account details.”
So do you know what to look out for to identify potential phishing scams? Telltale signs of these phishing email scams include punctuation as well as grammatical errors. Phishing emails can also be spotted as they come from unofficial email addresses and sometimes use outdated or incorrect logo and colour schemes.
Emails or messages that request you to enter your credit card information or other sensitive information should raise concerns. Should you encounter any of these scenarios it is always best to close the email then go to the official site. Once on the official site you can check to see if the issues mentioned in the email are valid. You can also contact the company’s support team.
Should you happen to click on one of these links, delete the email contact the company via official channels and change your passwords. Also consider enabling two-step authentication wheenever possible. Scamwatch has more advice should you still be unsure what to do.